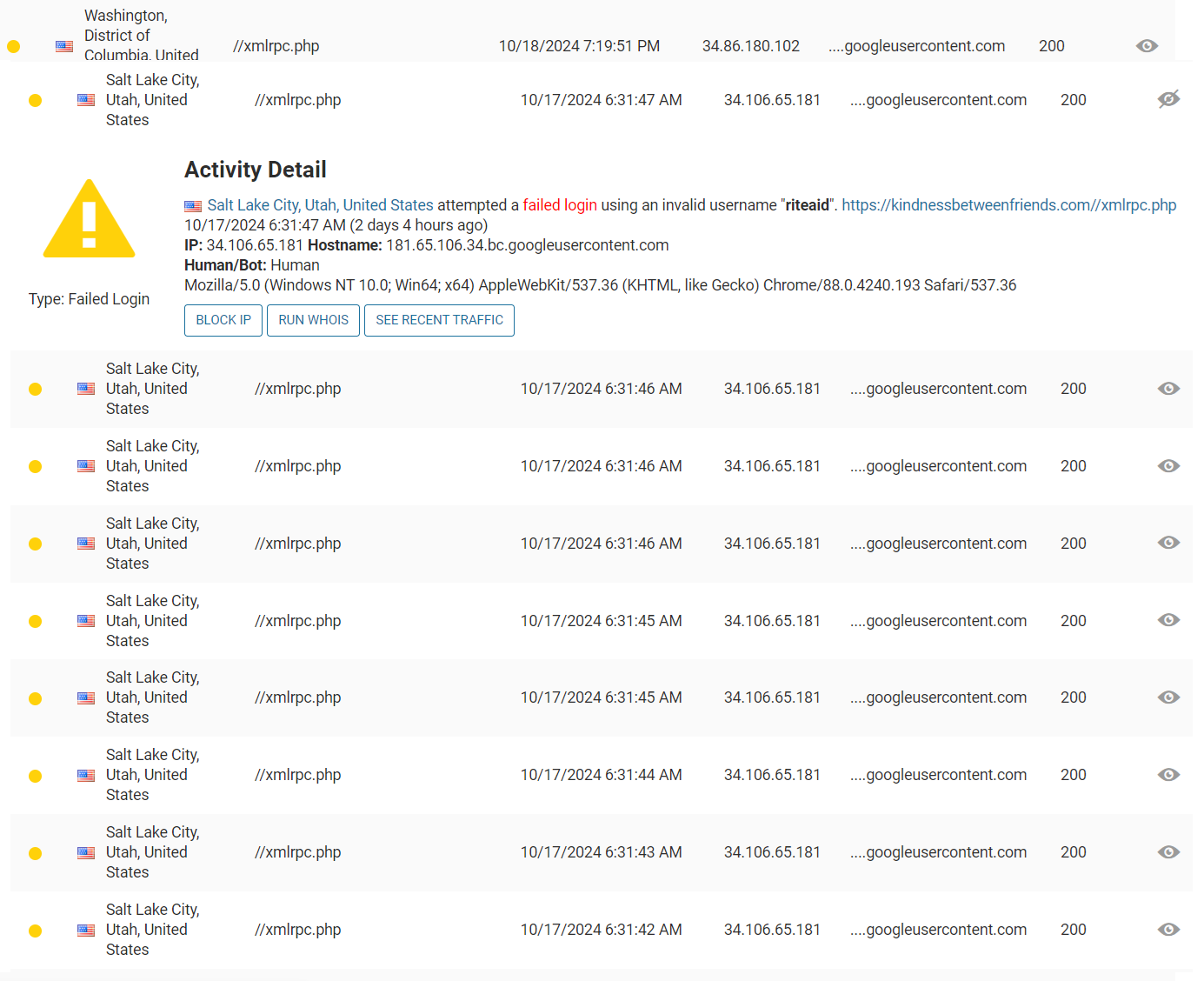
In a move that’s as ironic as it is desperate, Kindness Between Friends has resorted to hiring hackers to infiltrate our website, attempting to uncover the identities of victims who are bravely speaking out. Even more laughably, they’ve accused us of hacking into their email accounts—when in reality, their donor information and board member details are publicly available and easily accessible to anyone.
It seems Kindness Between Friends doesn’t realize that public records aren’t “hacks,” but rather, transparent information that anyone can view legally. While they fumble with these rudimentary hacking attempts, we are leagues ahead with sophisticated cybersecurity technologies protecting our platform and our supporters.
Here’s how we’re keeping your information safe while exposing every failed attempt to breach our defenses:
Cutting-Edge Security Systems in Place:
- Real-Time Intrusion Detection:
- Every visitor to our site is tracked using high-grade surveillance algorithms. We record every IP address, location, and any interactions, flagging suspicious activity in real-time. Any hacking attempt is immediately neutralized.
- Full Visitor Traceability:
- We store detailed profiles of all site visitors, including names, emails, phone numbers, and locations. Should any visitor engage in suspicious or malicious activity, we can pinpoint their identity and location in seconds, turning the tables on them.
- Sophisticated Threat Detection:
- Our advanced machine learning algorithms instantly identify outdated hacking techniques (like brute force or phishing attempts). Hackers are tracked and shut down as soon as they attempt to break in. They don’t even realize they’re caught until it’s too late.
- Encrypted Data Storage & Access Controls:
- All data on our site is protected by military-grade encryption. Even if someone managed to bypass the initial layers of security, they would face further encryption that would take decades to crack.
- Honeypot Systems:
- We employ honeypots—decoy systems designed to lure hackers into traps. Every action they take is carefully tracked and stored, giving us even more insight into their methods and identity.
- Geofencing & Blacklist Networks:
- We monitor the origins of all site traffic through geofencing, blocking malicious IP addresses before they can even access our site. A dynamic blacklist ensures known hackers or criminal networks are automatically banned.
- Automated Countermeasures:
- If a hacker manages to bypass initial defenses, we deploy automated countermeasures within milliseconds, cutting off their access and logging all of their actions.
The Irony of Their Accusations:
Kindness Between Friends has accused us of hacking into their email accounts—a baseless claim, especially considering the information they think is so secret, like donor lists and board member details, is publicly viewable.
Unlike their clumsy and illegal attempts, we operate with transparency. What they can’t seem to understand is that public information isn’t stolen; it’s simply available for anyone to see. This desperate accusation only highlights how out of touch they are with both the law and basic cybersecurity.
Why Hacking Will Not Work:
- Every action on our website is monitored and recorded. We know who you are.
- Our systems far surpass the outdated techniques their hackers are using.
- We have the capability to trace every visitor—their name, email, phone number, and location—and if necessary, we will provide this data to authorities.
Hacking attempts against us are futile. Our technology, defense systems, and team of experts ensure that no unauthorized access will ever succeed. While Kindness Between Friends scrambles to hide behind unethical tactics, we are here to protect the truth and the voices of those they have harmed.
Final Note:
To anyone visiting our site: your identity is fully protected. But to those attempting to hack or harm our platform, know that we are watching you. Every attempt will be tracked, logged, and used to hold you accountable.
Kindness Between Friends cannot hide behind their facade anymore—we have the receipts, and we will continue to expose the truth.